AP Location
With CoovaChilli managing the traffic of multiple access points, it can now be configured to utilize the MAC Authentication features found in some WLAN products to learn the access point location of a subscriber device. To demonstrate the use of this feature, hear is an example using both the Cisco Aironet and the Alcatel-Lucent/Aruba OmniAccess switch.
CoovaChilli with AP/switch MAC Authentication
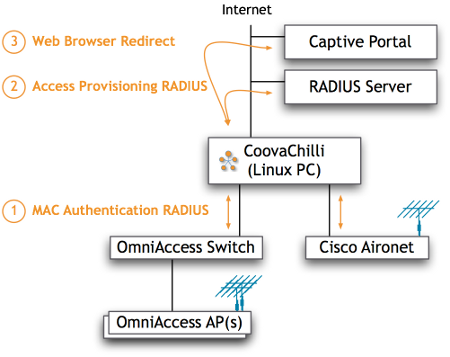
(1) The access point (or switch) performs a MAC authentication when the subscriber associates. CoovaChilli is configured to always reply with an Access-Accept after noting any Vendor Specific Attributes (VSAs) or the configured location attribute.
(2) Any VSAs plus ChilliSpot-Location, if a location attribute was specified, are sent in all RADIUS for the session.
(3) If the location attribute was specified, the loc=attribute-value query string parameter is sent to the captive portal in the initial redirect.
Cisco Aironet Example
The Cisco Aironet is able to provide multiple wireless networks and can put them on one or more VLAN networks. In this example, we configure the Cisco with one wireless signal configured with MAC Authentication. CoovaChilli is then setup to provide RADIUS services using it’s proxyport (same port used for EAP/802.1x proxy) and to always reply with a RADIUS Access-Accept to MAC authentication requests. Additionally, CoovaChilli is configured to use the NAS-Identifier attribute sent by the Cisco as the location attribute.
Configuring the Cisco Aironet 1200
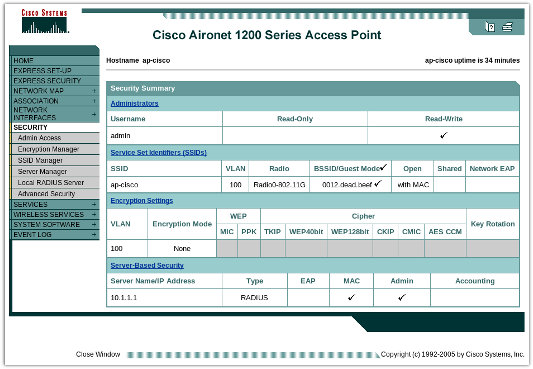
Shown above is an overview of the Cisco configuration under the Security menu. In our case, we have a single wireless network with SSID ap-cisco that is configured with MAC authentication. We additionally have a RADIUS server defined, which is configured to use the CoovaChilli proxy settings.
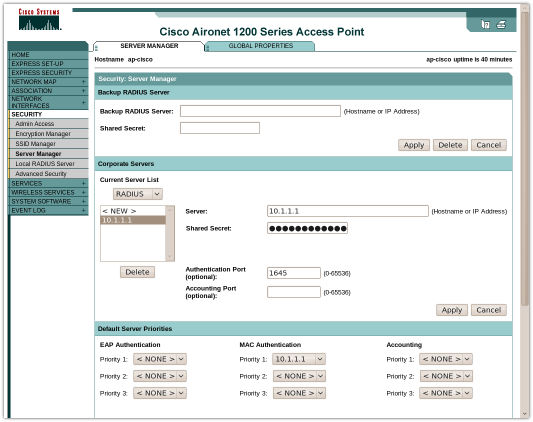
Under Server Manager, we have a single RADIUS server using the CoovaChilli proxy configurations (listen IP, port, and secret).
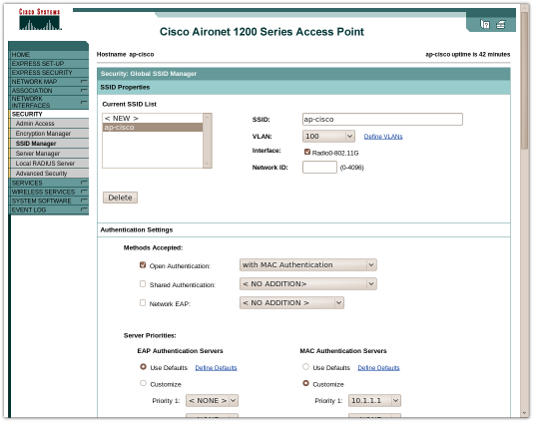
Under SSID Manager, we then have a wireless signal configured with Open Authentication with MAC Authentication.
CoovaChilli Configuration
The RADIUS settings of the Cisco are that of the CoovaChilli proxy port. In this case, CoovaChilli will be listening on 10.1.1.1 port 1645 and with RADIUS shared secret my-secret. CoovaChilli is configured to get the location attribute NAS-Identifier (type 32) from the Cisco, and to respond with an Access-Accept.
/etc/chilli/eth1.100/config:
HS_NASID=nas-100
HS_NETWORK=10.100.1.0
HS_NETMASK=255.255.255.0
HS_UAMLISTEN=10.100.1.1
HS_RADPROXY=on
HS_RADPROXY_LISTEN=10.1.1.1
HS_RADPROXY_CLIENT=10.1.1.0/24
HS_RADPROXY_SECRET=my-secret
HS_RADPROXY_PORT=1645
HS_RADPROXY_MACACCEPT=on
HS_RADPROXY_LOCATTR=32
...
RADIUS MAC Authentication Access-Request from Cisco
When a wireless client associates with the Cisco, it will do MAC authentication, sending information to CoovaChilli, which then responds with an Access-Accept.
AccessRequest:
User-Name (1) = 001124xxxxxx
User-Password (2) = [String](Encrypted)
Called-Station-Id (30) = 00-12-DA-XX-XX-XX
Calling-Station-Id (31) = 00-11-24-XX-XX-XX
Service-Type (6) = Login
NAS-Port-Type (61) = Wireless - IEEE 802.11
NAS-Port (5) = 264
NAS-IP-Address (4) = 10.1.1.2
NAS-Identifier (32) = ap-cisco
RADIUS Access-Request from CoovaChilli
After learning the location, CoovaChilli with then send the location information in all subsequent RADIUS for that session (MAC and UAM authentication) in the attribute ChilliSpot-Location.
AccessRequest:
ChilliSpot-Version = 1.2.3-rc1
User-Name = 00-11-24-XX-XX-XX
User-Password = [String](Encrypted)
Calling-Station-Id = 00-11-24-XX-XX-XX
Called-Station-Id = 00-06-4F-XX-XX-XX
NAS-Port = 1
NAS-IP-Address = 10.100.1.1
Service-Type = Framed-User
NAS-Identifier = nas-100
Acct-Session-Id = 4bc5bf4a00000001
NAS-Port-Type = Wireless-802.11
WISPr-Location-ID = isocc=,cc=,ac=,network=MyHotspot,100
WISPr-Location-Name = MyHotspot
ChilliSpot-DHCP-Parameter-Request-List = [Data](Binary)
ChilliSpot-DHCP-Client-Id = [Data](Binary)
ChilliSpot-DHCP-Hostname = iMac
ChilliSpot-Location = ap-cisco
Message-Authenticator = [Data](Binary)
Location in Initial Redirect
The location is also present in the initial redirect URL query string, as:
...&called=xx-xx-xx-xx-xx-xx&nasid=nas-100&loc=ap-cisco&...
Alcatel-Lucent OmniAccess Example
An example using the OmniAccess 4304 WLAN Switch from Alcatel-Lucent / Aruba.
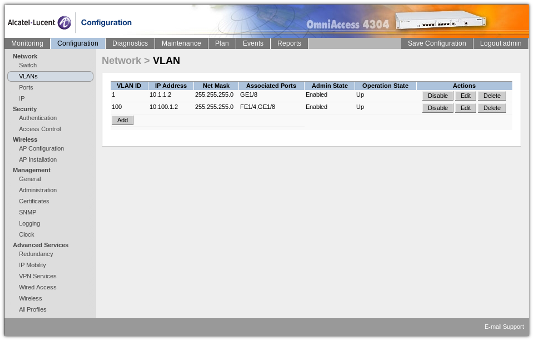
For the Network VLANs Configuration we have a simple setup with physical port 8 is our WAN port, and is given IP address 10.1.1.2. We then have a single VLAN setup on physical port 4, which has a subscriber network access point.
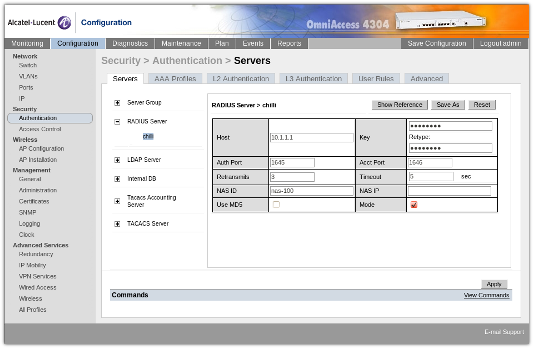
Under Security / Authentication / Servers, we have defined a single RADIUS server which points to our CoovaChilli RADIUS proxy port.
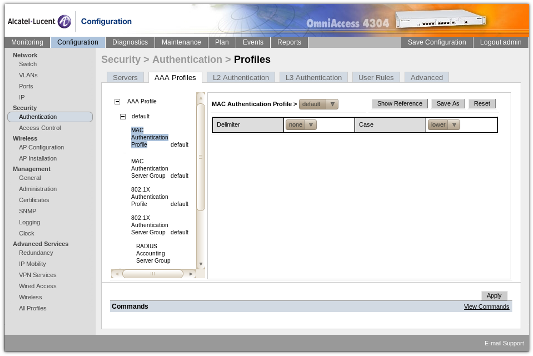
Under Security / Authentication / Profiles, ensure that the MAC Authentication profile is using default.
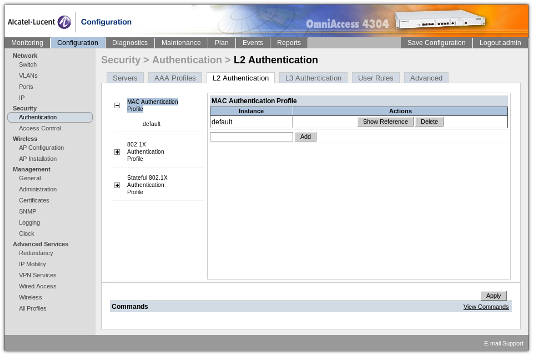
Under Security / Authentication / L2 Authentication, ensure that the MAC Authentication profiles has the default profile added.
Under Security / Authentication / Advanced, we configure the RADIUS client to be using the 10.1.1.2 IP address on the main interface.
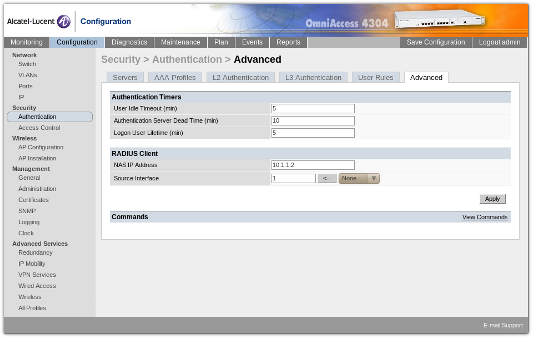
For more information on how to setup your OmniAccess, please refer to your users manual.
CoovaChilli Configuration
The RADIUS settings used in the switch are that of the CoovaChilli proxy port. In this case, CoovaChilli will be listening on 10.1.1.1 port 1645 and with RADIUS shared secret my-secret. CoovaChilli is configured location attribute Aruba-Location-Id (vendor 14823, type 6), and to respond with an Access-Accept.
/etc/chilli/eth1.100/config:
HS_NASID=nas-100
HS_NETWORK=10.100.1.0
HS_NETMASK=255.255.255.0
HS_UAMLISTEN=10.100.1.1
HS_RADPROXY=on
HS_RADPROXY_LISTEN=10.1.1.1
HS_RADPROXY_CLIENT=10.1.1.0/24
HS_RADPROXY_SECRET=my-secret
HS_RADPROXY_PORT=1645
HS_RADPROXY_MACACCEPT=on
HS_RADPROXY_LOCATTR="14823,6"
...
RADIUS MAC Authentication Access-Request from OmniAccess
When a subscriber associates to one of the access points, the switch sends CoovaChilli RADIUS similar to:
AccessRequest:
NAS-IP-Address = 10.1.1.2
NAS-Port = 0
NAS-Port-Type = Wireless-802.11
User-Name = 001124XXXXXX
User-Password = [String](Encrypted)
Calling-Station-Id = 001302XXXXXX
Called-Station-Id = 00064FXXXXXX
Service-Type = Login
Aruba-Essid-Name = ap-aruba
Aruba-Location-Id = ap-aruba
NAS-Identifier = nasname
The Vendor Specific Attributes (those starting with Aruba-) are then associated with the session and are used in CoovaChilli authentication.
RADIUS Access-Request from CoovaChilli
In our example, we also have chilli configured to use the Aruba-Location-Id as our ChilliSpot-Location. An example CoovaChilli MAC authentication after accepting the MAC authentication from the OmniAccess:
AccessRequest:
ChilliSpot-Version = 1.2.3-rc1
User-Name = 00-11-24-XX-XX-XX
User-Password = [String](Encrypted)
Calling-Station-Id = 00-13-02-XX-XX-XX
Called-Station-Id = 00-06-4F-XX-XX-XX
NAS-Port = 1
NAS-IP-Address = 10.100.1.1
Service-Type = Framed-User
NAS-Identifier = nas-100
Acct-Session-Id = 4bc5bf4a00000001
NAS-Port-Type = Wireless-802.11
WISPr-Location-ID = isocc=,cc=,ac=,network=MyHotspot,100
WISPr-Location-Name = MyHotspot
ChilliSpot-DHCP-Parameter-Request-List = [Data](Binary)
ChilliSpot-DHCP-Client-Id = [Data](Binary)
ChilliSpot-DHCP-Hostname = iMac
Aruba-Essid-Name = ap-aruba
Aruba-Location-Id = ap-aruba
ChilliSpot-Location = ap-aruba
Message-Authenticator = [Data](Binary)
Location in Initial Redirect
Just like with the Cisco, the location is also sent in the initial redirect URL.
...&called=xx-xx-xx-xx-xx-xx&nasid=nas-100&loc=ap-aruba&...
This feature requires CoovaChilli 1.2.3.
